To start Wallet Manager,go to
Start -> Programs -> OracleAS 10g - ORACLE_HOME -> Integrated Management Tools -> Wallet Manager
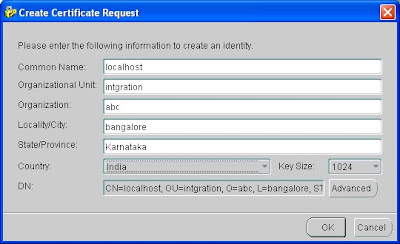
Create a new wallet
Select Wallet -> New
Enter a password for the wallet
Specify Wallet Type: Standard
And say yes
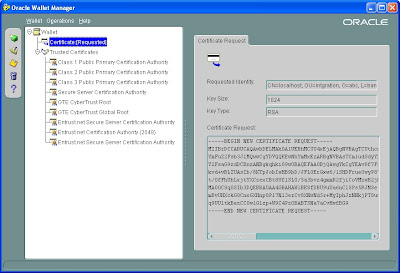
Export the certificate to some local file directory
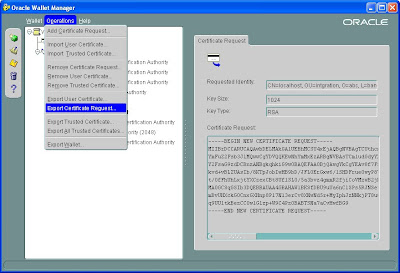
Save the certificates with .cer format
Create a new directory where in you will store all the files.
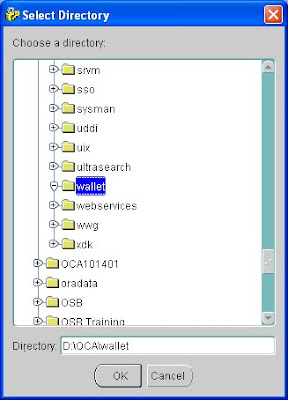
Open the .csr file thus created and copy the contents of the certifícate
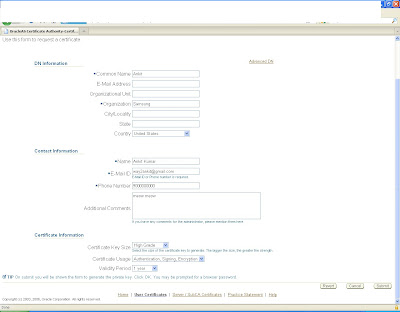
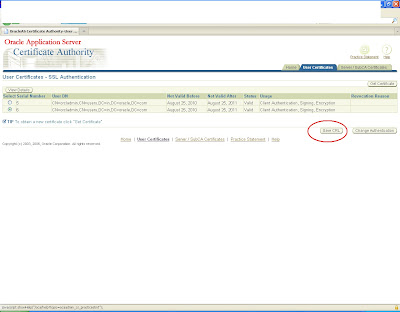
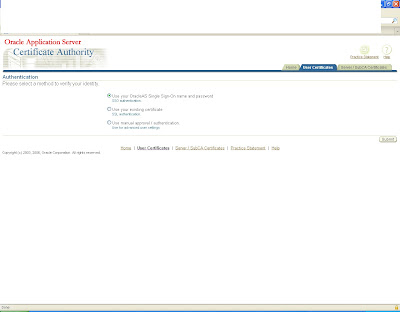
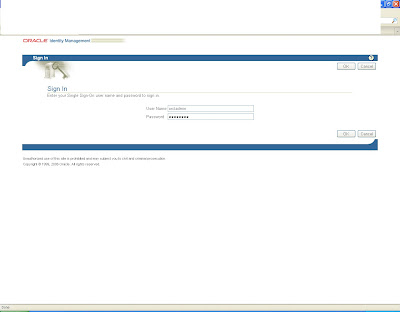
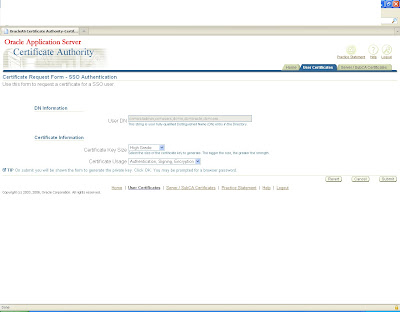
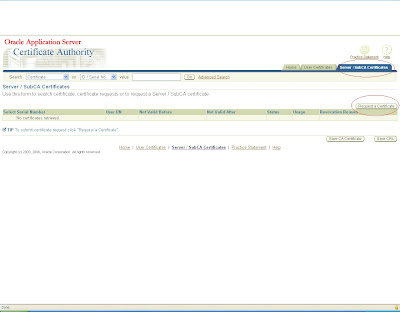
Log in to https:host:sslport/oca/user
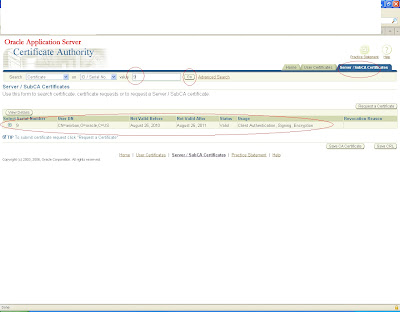
Navigate to Server/sub ca certificates
and create a new request
copy the content of certificate to pkcs request
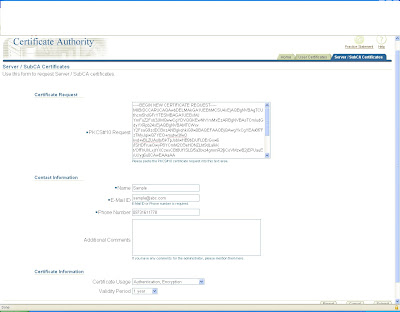
and submit the request
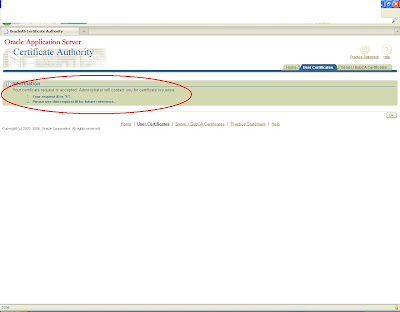
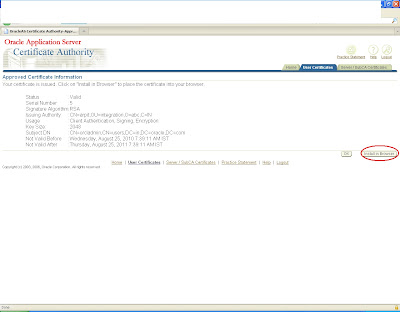
You will get a request corresponding to that as shown
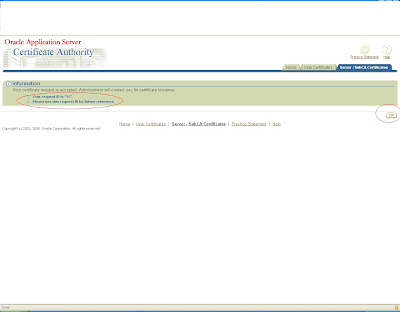
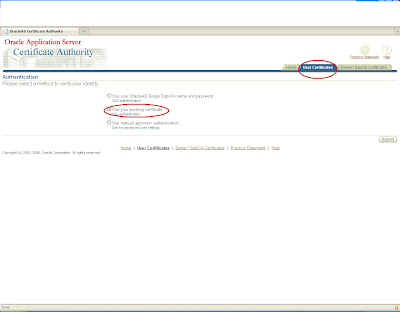
now log in to admin page by logging in to
https:host:sslport/oca/admin and switch to certificate management tab
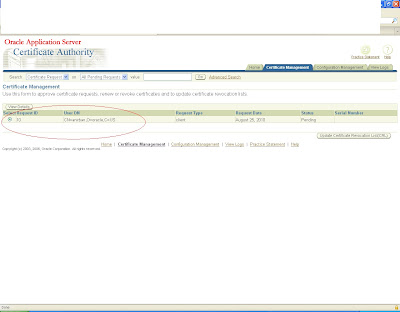
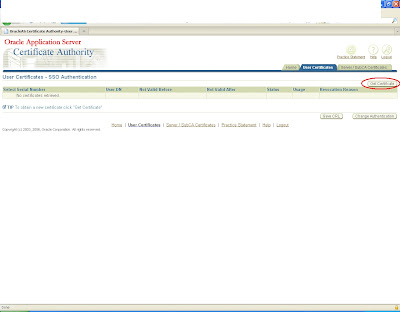
There you will get a pending request with the same user id for which certificate has been requested.
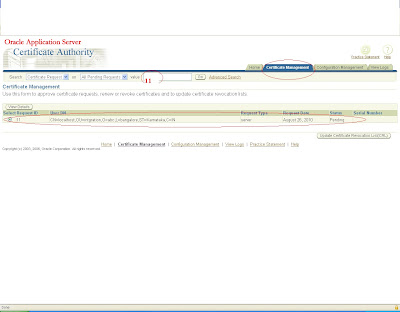
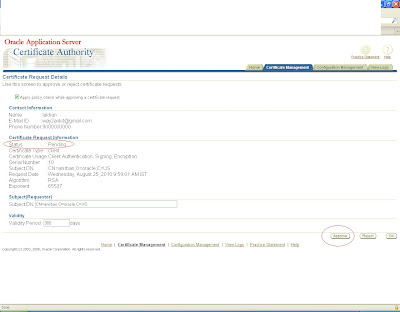
click on view button and approve it.
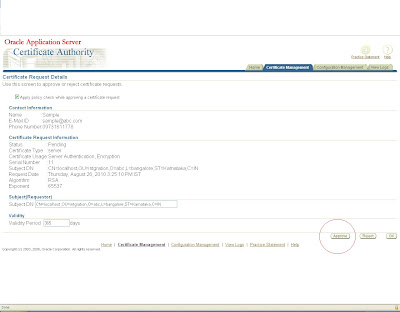
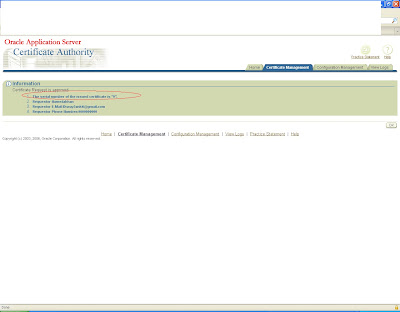
it will again generate a certificate with some certificate id
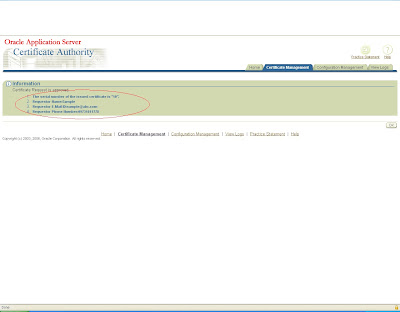
copy this certification id and now log in to the user console
https:host:ssport/oca/user
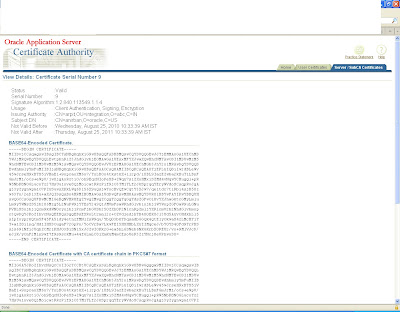
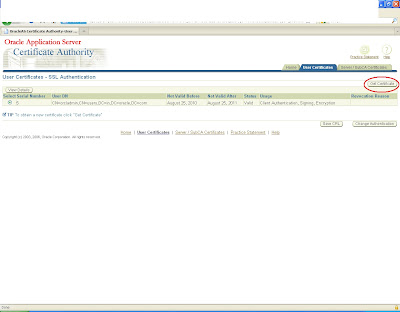
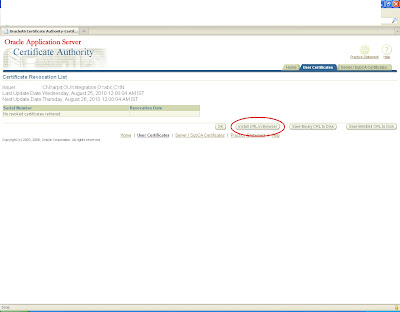
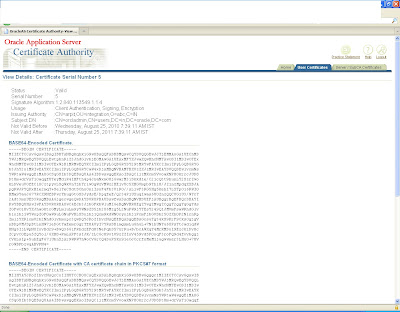
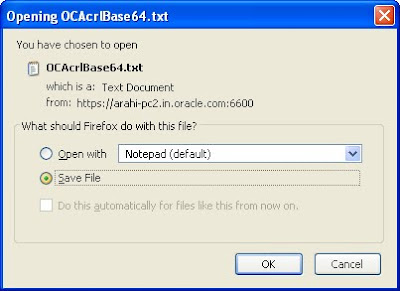
and move to server/sub ca certificates and search with the certification id you will get it in the list now save this CA certificate as .crt file in the same location.
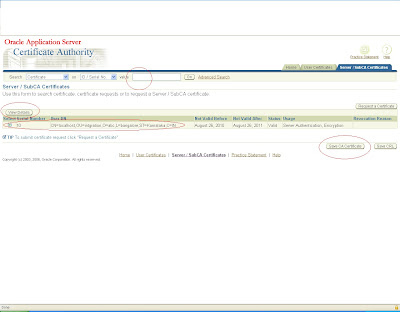
Again click on view details and view the certificate
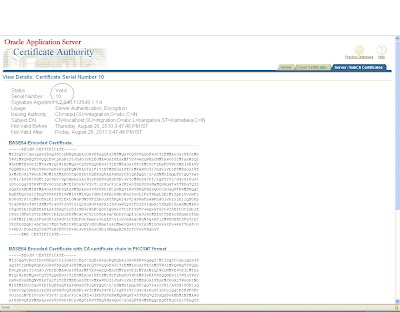
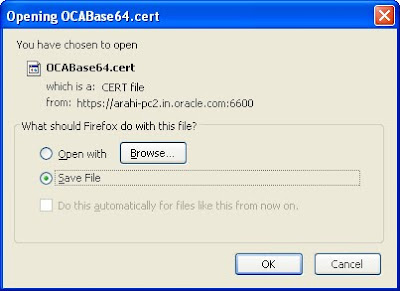
This certificate will be saved as a base certificate
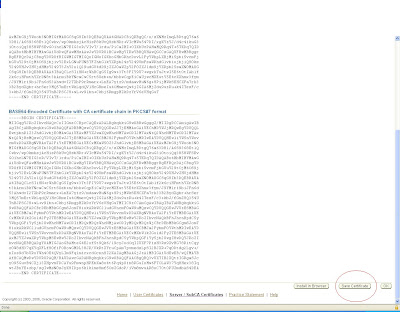
Similarly the ca certificate will be saved as a root certificate
Now once you have the certificate you can import it back to your wallet manager to change its status from pending to ready.
This can be done like this.
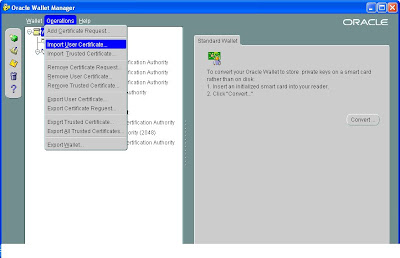
Now select the certificate which you have created
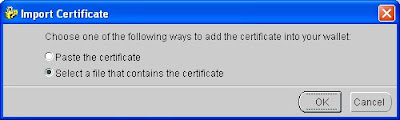
Well this really didn't worked for me as it was giving some error that ca certificate doesn't exist.
I left the plan to authenticate is from oca as OCA is not a product from 11g.
SO i rather gave the certification request to verisign,i used the trail version to get my certificate validated.
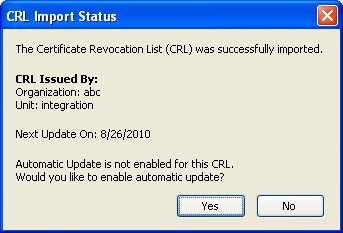
ONce validate when you will import your certificate status will be changed to ready
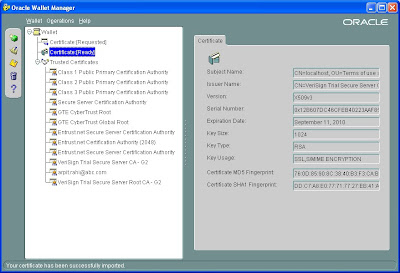
You can see that the issuer is Verisign trial version and it has also added some verisign trusted certificate.
There are other certification authority also but i am aware of verisign only you can do a google search and send your certificate to them to get it verified.
I believe now you have got some idea of how a certification authority works how wallet manager raise a certification request and how it is verified and completed.